ЛР 4.7 - Интеграция почтового сервера с Samba AD DC
Официальная документация iRedMail https://docs.iredmail.org/active.directory.html
На lin-dc создайте новую А-запись в DNS:
samba-tool dns add lin-dc lab.lan mail A 10.20.30.2 -U Administrator
Установка почтового сервера iRedMail
- Склонируйте tmpl-ubuntu24-server в новую ВМ mail (FQDN - mail.lab.lan, ip - 10.20.30.2):
- Установите дополнительные пакеты:
apt update && apt install gzip dialog - Скачайте архив с официального сайта iRedMail и распакуйте его:
wget https://github.com/iredmail/iRedMail/archive/refs/tags/1.7.1.tar.gz
tar zxf 1.7.1.tar.gz - Перейдите в разархивированную директорию и запустите установочный скрипт:
cd iRedMail-1.7.1/
bash iRedMail.sh - В процессе установки выберите в качестве бэкенда OpenLDAP, а в качестве почтового домена укажите lab.lan.
- После установки от имени пользователя postmaster@lab.lan проверьте работоспособность почты по вдресу https://mail.lab.lan/
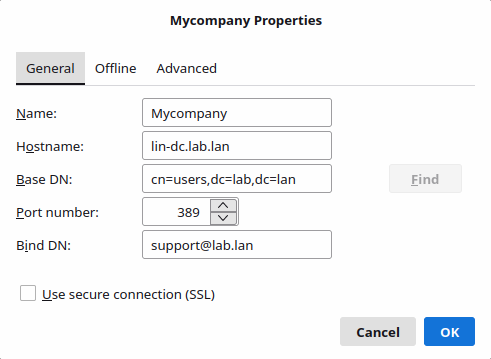
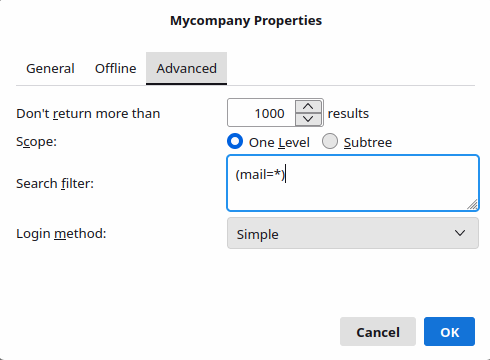
Подготовка Samba AD DC
- На ВМ lin-dc создайте нового доменного пользователя vmail:
samba-tool user create vmail 'Specialist1!' --given-name 'Vmail' --surname 'Iredmail' - Отредактируйте конфиг /etc/samba/smb.conf:
[global]
ldap server require strong auth = no
...- Перезапустите ВМ lin-dc.
- На ВМ mail проверьте работоспособность запросов от пользователя vmail:
ldapsearch -x -H ldap://lab.lan -D 'LAB\vmail' -W -b 'cn=users,dc=lab,dc=lan'
Настройка POSTFIX
- Отключите лишние модули:
postconf -e virtual_alias_maps=''
postconf -e sender_bcc_maps=''
postconf -e recipient_bcc_maps=''
postconf -e relay_domains=''
postconf -e relay_recipient_maps=''
postconf -e sender_dependent_relayhost_maps='' - Укажите домен для следующих модулей:
postconf -e smtpd_sasl_local_domain='lab.lan'
postconf -e virtual_mailbox_domains='lab.lan' - Настройте остальные модули:
postconf -e transport_maps='hash:/etc/postfix/transport'
postconf -e smtpd_sender_login_maps='proxy:ldap:/etc/postfix/ad_sender_login_maps.cf'
postconf -e virtual_mailbox_maps='proxy:ldap:/etc/postfix/ad_virtual_mailbox_maps.cf'
postconf -e virtual_alias_maps='proxy:ldap:/etc/postfix/ad_virtual_group_maps.cf' - Удалите строки в /etc/postfix/main.cf:
check_policy_service inet:127.0.0.1:7777- Отредактируйте (или создайте) файл /etc/postfix/transport и прочтите его утилитой postmap:
lab.lan dovecotpostmap hash:/etc/postfix/transport
- Создайте конфиги для взаимодействия Postfix и Samba AD DC:
nano /etc/postfix/ad_sender_login_maps.cf
server_host = lin-dc.lab.lan
server_port = 389
version = 3
bind = yes
start_tls = no
bind_dn = LAB\vmail
bind_pw = Specialist1!
search_base = cn=users,dc=lab,dc=lan
scope = sub
query_filter = (&(userPrincipalName=%s)(objectClass=person)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
result_attribute= userPrincipalName
debuglevel = 0nano /etc/postfix/ad_virtual_mailbox_maps.cf
server_host = lin-dc.lab.lan
server_port = 389
version = 3
bind = yes
start_tls = no
bind_dn = LAB\vmail
bind_pw = Specialist1!
search_base = cn=users,dc=lab,dc=lan
scope = sub
query_filter = (&(objectclass=person)(userPrincipalName=%s))
result_attribute= userPrincipalName
result_format = %d/%u/Maildir/
debuglevel = 0nano /etc/postfix/ad_virtual_group_maps.cf
server_host = lin-dc.lab.lan
server_port = 389
version = 3
bind = yes
start_tls = no
bind_dn = LAB\vmail
bind_pw = Specialist1!
search_base = cn=users,dc=lab,dc=lan
scope = sub
query_filter = (&(objectClass=group)(mail=%s))
special_result_attribute = member
leaf_result_attribute = mail
result_attribute= userPrincipalName
debuglevel = 0Проверка интеграции POSTFIX и SAMBA
postmap -q support@lab.lan ldap:/etc/postfix/ad_sender_login_maps.cf
postmap -q support@lab.lan ldap:/etc/postfix/ad_virtual_mailbox_maps.cf
postmap -q group@lab.lan ldap:/etc/postfix/ad_virtual_group_maps.cf
Если на запросы получены корректные ответы - перезапустите postfix
systemctl restart postfix
Настройка Dovecot
- Отредактируйте конфиг /etc/dovecot/dovecot-ldap.conf:
hosts = lab.lan:389
ldap_version = 3
auth_bind = yes
dn = vmail@lab.lan
dnpass = Specialist1!
base = cn=users,dc=lab,dc=lan
scope = subtree
deref = never
iterate_attrs = userPrincipalName=user
iterate_filter = (&(userPrincipalName=*)(objectClass=person)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
user_filter = (&(userPrincipalName=%u)(objectClass=person)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
pass_filter = (&(userPrincipalName=%u)(objectClass=person)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
pass_attrs = userPassword=password
default_pass_scheme = CRYPT
user_attrs = mail=master_user,mail=user,=home=/var/vmail/vmail1/%Ld/%Ln/,=mail=maildir:~/Maildir/- Перезапустите dovecot:
systemctl restart dovecot
Проверка интеграции DOVECOT и SAMBA
nc localhost 143 или telnet localhost 143
. login support@lab.lan Specialist1!
Настройка SoGo
Отредактируйте конфиг /etc/sogo/sogo.conf:
SOGoUserSources = (
{
// Used for user authentication
type = ldap;
id = users;
canAuthenticate = YES;
isAddressBook = NO;
displayName = "LDAP Authentication";
hostname = "ldap://lab.lan:389"; // <- Set to ldaps://ad.example.com:636 for LDAPS.
baseDN = "cn=users,dc=lab,dc=lan";
bindDN = "vmail@lab.lan";
bindPassword = "Specialist1!";
filter = "objectClass=person AND userPrincipalName='*' AND (NOT userAccountControl:1.2.840.113556.1.4.803:=2)";
scope = SUB;
// always keep binding to the LDAP server using the DN of the
// currently authenticated user. bindDN and bindPassword are still
// required to find DN of the user.
// Note: with default LDAP acl configured by iRedMail, user doesn't
// have privilege to query o=domains,dc=delmsgs,dc=freeddns,dc=org.
// so this doesn't work.
bindAsCurrentUser = YES;
// The algorithm used for password encryption when changing
// passwords without Password Policies enabled.
// Possible values are: plain, crypt, md5-crypt, ssha, ssha512.
userPasswordAlgorithm = ssha512;
CNFieldName = cn;
IDFieldName = userPrincipalName;
// value of UIDFieldName must be unique on entire server
UIDFieldName = userPrincipalName;
IMAPLoginFieldName = userPrincipalName;
MailFieldNames = (userPrincipalName);
bindFields = (userPrincipalName);
},
{
// Used for global address book
type = ldap;
id = global_addressbook;
canAuthenticate = NO;
isAddressBook = YES;
displayName = "Global Address Book";
bindAsCurrentUser = YES;
// Listing of this LDAP source is only possible when performing a
// search (respecting the SOGoSearchMinimumWordLength parameter)
// or when explicitely typing a single dot.
// Defaults to YES when unset.
//
// WARNING: if you have many accounts in this address book, it may
// reach server-side query size limit, or cause
// performance issue.
listRequiresDot = NO;
// Set to ldaps://ad.example.com:636 for LDAPS.
hostname = "ldap://lab.lan:389";
baseDN = "cn=users,dc=lab,dc=lan";
bindDN = "vmail@lab.lan";
bindPassword = "Specialist1!";
filter = "(objectClass=person OR (objectClass=group AND mail='*')) AND (NOT userAccountControl:1.2.840.113556.1.4.803:=2)";
scope = SUB;
IDFieldName = userPrincipalName;
bindFields = (userPrincipalName);
// value of UID field must be unique on whole server.
UIDFieldName = userPrincipalName;
IMAPLoginFieldName = userPrincipalName;
CNFieldName = cn;
SearchFieldNames = (mail, cn, sAMAccountName, displayName, sn, givenName);
mapping = {
ou = ("department", "ou");
street = ("streetAddress", "street");
mozillaworkurl = ("wWWHomePage", "mozillaworkurl");
description = ("info", "description");
};
}
);
Управление пользователями
- Создайте нового пользователя, указав его email:
samba-tool user create aho 'Specialist1!' --given-name 'Svirid' --surname 'Drakonovich' --mail-address 'aho@lab.lan'
- Отредактируйте существующего пользователя, заполнив для него значение email (для отображения в адресной книге).
samba-tool user edit support --editor=nano
mail: support@lab.lan- Самостоятельное задание - настройте на lin-client почтовый клиент Thunderbird.
- Подключите адресную книгу домена Samba к Thinderbird: